The price of publishing certified, code signed software for Microsoft Windows quadrupled this year. Apple developers have remained at $99 a year as code signing is apart of their membership fees; whether or not one wishes to distribute privately or through the AppStore. Microsoft on the other hand has been slow to compete and while the price of Microsoft’s developer program is only $19 dollars a year it does not include code signing services for distribution (unless one qualifies and distributes solely through Microsoft’s Store). Instead, for Windows developers that wish to distribute code through their own store, website, or organization can obtain a certificate from a CA (certificate authority) and can expect to pay over $875 dollars a year for a trusted CA like Digicert1. That could easily exceed thousands of dollars over a product’s lifespan. The price hike may cause open source authors to rethink the costs associated with releasing their finished binaries; leaving end users without a safe way to install their creations or worse, expose them to potentially harmful, tampered distributions.
Don Ho, open source developer and creator of the popular Notepad++ application for Windows decided to drop CA code signing (although as of this writing, it appears his distribution is signed with a valid CA again). Notepad++ enjoys the compliments of a donated certificate from a popular CA, but such certificates are not awarded to just any developer and there are no rules that surround who gets a free certificate and who doesn’t. For open source developers that have typically a paltry to zero profit margin; the extra costs are a great inhibitor to distribution.
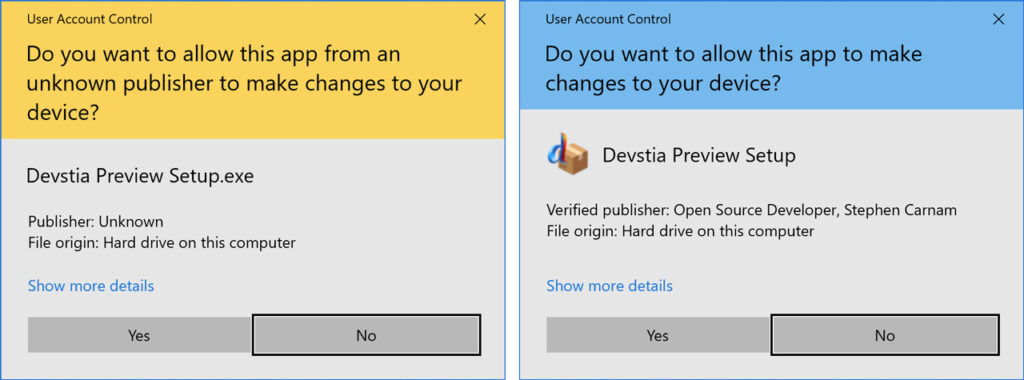
Why does this matter? For Windows users, installing new software invokes a blue confirmation message indicating “Verified Publisher” for code signed with a valid certificate, or a yellow warning saying “Publisher: Unknown”; the result of code signed with an invalid, revoked, or otherwise missing certificate. While a few users may not care about the validation message (they should), many companies and organizations require it. Some anti-malware applications may prevent the installation of unsigned code altogether. It is akin to taking medication from a package with the tamper seal in place; versus an unacceptable “open box”. It’s typically better to have one’s code properly signed with a valid certificate from a trusted certificate authority. This at least provides some assurance that the software hasn’t been modified or altered (for instance by a computer virus) since the time the author originally packaged it for user installation.
This price hike was the result of new industry guidelines that first took effect on December 9, 2019 and more stringent changes in June 2023. For the decade prior, code signing costs were fairly steady. A code signing certificate from Comodo, a popular code signing certificate authority, was less than $99 in 20102 and a quick look at the Internet Archive Wayback Machine shows us that the same certificate “on sale” from Comodo at just $833. The new guideline changes now require all certificates to be stored on hardware compliant device (“FIPS 140 Level 2, Common Criteria EAL 4+, or equivalent”); this means secure physical media usually accessed by a USB dongle by the computer wanting to sign code. A software author wanting to sign their code for distribution has to have this new hardware; and shipping hardware equals higher costs. While the hardware itself should only increase the costs by $20 to $40; the monopolies of certificate authorities have all raised their prices. Securely publishing content on the web (mostly text and words) has generally gotten cheaper thanks to free SSL certificates from the Let’s Encrypt non-profit organization; but the outlook looks grim for open source code developers that wish to do the same with their programs and applications.
Mafia as Google’s dictionary box defines it: “…an organized international body of criminals”. Probably the least appealing name one wants to hear when trying to submit their personal identification information.
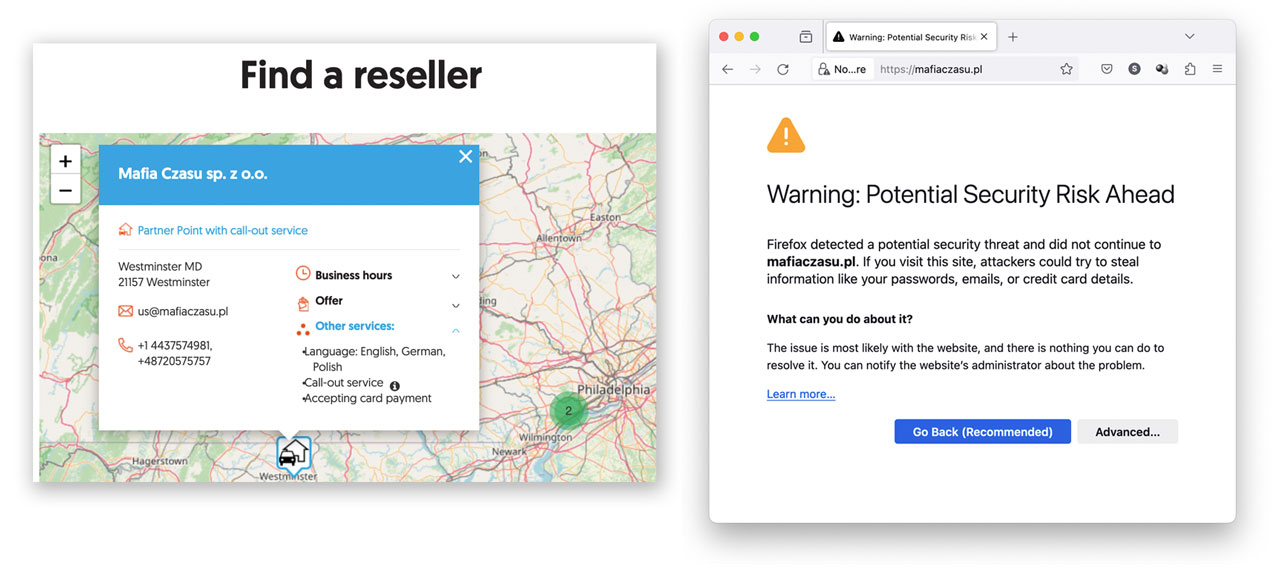
However, it turns out there is one (and only one AFAIK) legitimate CA that issues certificates at a reduced cost specifically for individual open source developers. That company is Certum, a Polish multinational software company. They’ve even figured out a way to get around the hardware requirement by virtualizing access through the use of your own qualifying iPhone/Android mobile device. The process is referred to as “cloud code signing” and eliminates the need to ship physical hardware (and reduces cost). The price, just $50 dollars. Unfortunately the onboarding process is terrible. While Certum is certainly a legitimate certificate authority; the process to validate for the certificate and actually perform the code signing task is complicated by a lack of Polish to English translated material and comically titled western representatives of the Eastern European nation. Following the verification link on the product page leads you to what should be straight forward requirements: government identification, a recent utility bill, etc. Those items are listed but the first item suggests physical identity confirmation through a reseller. The only reseller in the United States is located in just six east coast locations; all the same individual: Mafia Czasu. Mafia as Google’s dictionary box defines it: “…an organized international body of criminals”. Probably the least appealing name one wants to hear when trying to submit their personal identification information. Worse, the reseller’s own website lacks a valid SSL certificate. Shouldn’t an SSL vendor have a valid SSL themselves?
If you want to get a certificate as an open source developer; skip the reseller route. Simply make a purchase for the product on Certum’s product page and then use the order number you get via email to correspond with Certum directly. Send in your identification materials (I used my driver license and utility bill) as a PDF file, zipped up and password protected. Be sure to password protect the zip file; on macOS this was easy using the command line. Send the information as suggested on their website to ccp@certum.pl. Next, just call their international support number during their business hours (9 hours ahead for me), ask for English, and tell them you’d like to give them the password for your certificate identification email attachment. Soon after, your online account purchase status will change from verifying to verified. But you are not out of the woods yet. You’ll eventually receive a plethora of emails and links with directions to install the mobile app, the desktop app (on the Windows computer that will be performing the code signing), and further activation instructions. While the links are in English, the destinations and screenshots are still in Polish.
You are better of using Google Translate, but not the one on your web browser or computer. Rather, use the Google Translate mobile app that is free and features an augmented reality mode. This enables you to hold your phone up to your computer monitor to translate the various native Polish buttons and links while your other free hand can use the mouse to click on them. In my case, and at the time of this writing, I made the mistake of clicking the English option in the upper right hand corner of Certum’s website; but this kicks you out of whatever context page you are on and sends you to a general knowledge base. Hint: I had to use a trusted ‘administrator’ command line prompt to eventually run signtool; this step was not mentioned.
With luck and navigating Microsoft’s documentation for the signtool command, you’ll be able to eventually use your new Certum issued certificate to code sign your release binaries for Microsoft Windows and get that blue “Verified Publisher” message box. Hopefully without being too blue in the face.
Cited sources:
- Digicert Order Page sampled on December 1, 2023
https://order.digicert.com/step1/code_signing_ev ↩︎ - Getting started with code signing for under $100 by Jeff Wilcox, February 27, 2010
https://jeff.wilcox.name/2010/02/codesigning101/ ↩︎ - Code Signing Certificate Comparison by Cheap SSL Security, January 31, 2023
https://web.archive.org/web/20230131071050/https://cheapsslsecurity.com/sslcompare/code-signing-comparison.html ↩︎
